Die neuesten Daten der IT-Forensik-Dienstleiter Coveware zeigen, dass die Zahl der Opfer von Ransomware-Angriffen, die sich für die Zahlung des Lösegelds entscheiden, stark zurück gegangen ist - zumindest zeitweise. Anfang 2019 zahlten 85% der Opfer von Ransomware-Angriffen nach einem Angriff ein Lösegeld. Mitte 2021 war der Prozentsatz auf 46% gesunken....
Blog.

weiterlesen
Ende 2023 befragte ein unabhängiges Forschungsunternehmen 1.200 IT-Führungskräfte und -Implementierer zu einem breiten Spektrum ihrer Datenschutzherausforderungen und -strategien. Dies ist die fünfte jährliche Veröffentlichung des Berichts "Data Protection Trends", um die Herausforderungen und Treiber der Datenschutzbranche zu quantifizieren. Die bemerkenswertesten Erkenntnisse sind:
Zuverlässigkeit und Konsistenz (beim Schutz von IaaS- und...

weiterlesen
Das Jahr 2023 dürfte das erfolgreichste Jahr für Ransomware-Gruppen in der Geschichte sein. Eine der häufigsten Bedrohungen für Unternehmen weltweit forderte dieses Jahr 4.368 Opfer - ein Anstieg von über 55,5% seit dem letzten Jahr. Allein Q2 und Q3 forderten mit 2.903 Opfern mehr Opfer als im gesamten Jahr 2022.
...

weiterlesen
Dem Data Protection Trends Report 2023 zufolge waren 85% der Unternehmen in den vorangegangenen zwölf Monaten von mindestens einem Cyberangriff betroffen - ein Anstieg gegenüber 76% im Vorjahr.
In der Umfrage wurde nach den Auswirkungen von Ransomware auf ihre Umgebungen sowie nach den künftigen IT-Strategien und Datenschutzinitiativen gefragt.Während die Analysten...

weiterlesen
Von der Alarmierung von Rettungskräften über den Zahlungsverkehr bis hin zur Stromversorgung - Kritische Infrastrukturen (KRITIS) sind für unsere Gesellschaft unverzichtbar. Wir alle sind im Alltag und vor allem in Extremsituationen darauf angewiesen. Die Verfügbarkeit kritischer Infrastrukturen sichert nicht nur die Handlungsfähigkeit staatlicher Institutionen, sondern ist auch die Voraussetzung für...

weiterlesen
Die jährliche von Sophos in Auftrag gegebene Studie, die sich mit den konkreten Ransomware-Erfahrungen von IT- und Cybersecurity-Führungskräften befasst, verdeutlicht die Realitäten, mit denen Unternehmen im Jahr 2023 konfrontiert sind. Sie zeigt die häufigsten Ursachen für Angriffe auf und beleuchtet, wie sich die Erfahrungen mit Ransomware je nach Unternehmensumsatz unterscheiden....

weiterlesen
Bewertung der Sicherheitsrisiken von Unternehmensspeichern & Backup-Systemen
Der Forschungsbericht 2023 enthält eine Analyse der IT-Sicherheitsrisiken in Unternehmen. Dazu wurden anonymisierte Daten aus einer großen Anzahl von Risikobewertungen für Speicher- und Backup-Systeme im Jahr 2022 zusammengetragen, um einen einzigartigen Einblick in den Stand der Speicher- und Backup-Sicherheit zu geben. Die automatisierte...

weiterlesen
Bedrohungsakteure setzen zunehmend Erpressungstechniken ein, um Einfluss auf Zielorganisationen zu nehmen und ihre Zwecke zu erfüllen. Während Ransomware in den letzten Jahren viel Aufmerksamkeit geschenkt wurde, setzen moderne Bedrohungsakteure zunehmend zusätzliche Erpressungstechniken ein, um Opfer zur Zahlung zu zwingen - oder sie verzichten ganz auf Ransomware und praktizieren eigenständig Erpressung.In...

weiterlesen
Ende 2022 schloss ein unabhängiges Marktforschungsunternehmen seine Umfrage unter 4.200 unabhängigen IT-Führungskräften und -Implementierern zu einer Vielzahl von Treibern, Herausforderungen und Strategien im Bereich Datensicherheit ab. Der Datensicherheit-Trendbericht ist in drei Abschnitte gegliedert:Makrotrends in der DatensicherheitCyberangriffe und andere AusfälleBetrachtung der Cloud
1. Makrotrends in der Datensicherheit
Dieses Diagramm umfasst mehr...

weiterlesen
Im Mai 2022 beauftragte die Firma Proofpoint, ein amerikanisches Unternehmen, das Software-as-a-Service sowie Produkte für E-Mail-Sicherheit und -Archivierung, Verhinderung von Datenverlust, elektronische Erkennung anbietet, die Non-Profit-Organisation CSA mit der Entwicklung einer Umfrage, um das Wissen, die Einstellungen und die Meinungen der Branche in Bezug auf Cloud- und Web-Bedrohungen besser zu...
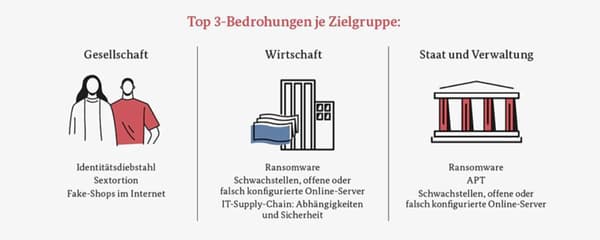
weiterlesen
Das Bundesamt für Sicherheit in der Informationstechnik (BSI) als Cybersicherheitsbehörde des Bundes veröffentlicht jährlich in seinem Bericht zur Lage der IT-Sicherheit in Deutschland einen umfassenden Überblick über Bedrohungen im Cyberspace. Der diesjährige Report bewertet auch den Stand der IT-Sicherheit im Kontext des russischen Angriffskriegs in der Ukraine.
“Die Bedrohungslage im...

weiterlesen
Deutsche Nutzer machen sich zunehmend Sorgen um die IT-Sicherheit und haben weniger Vertrauen in bestehende Vorkehrungen. Eine IDC-Umfrage unter 206 Sicherheitsexperten und Benutzern aus allen Branchen und Unternehmen aller Größen im September 2022 ergab, dass 60% besorgt über eine Verschlechterung der Sicherheitslage sind. Nur 65% fühlten sich gut geschützt -...

weiterlesen
Mit Unterstützung von Proofpoint befragte das Ponemon Institute 641 IT- und IT-Sicherheitsexperten in Gesundheitsorganisationen, die für die Umsetzung von Cybersicherheitsstrategien, einschließlich der Festlegung von IT-Cybersicherheitsprioritäten, der Verwaltung von Budgets und der Auswahl von Anbietern und Auftragnehmern verantwortlich sind.Laut der Studie waren 89 Prozent der untersuchten Organisationen in den letzten 12...

weiterlesen
Die von IDC in Zusammenarbeit mit Quantum veranlasste Umfrage “Data Deluge: Why Every Enterprise Needs a Cold Storage Strategy” befasst sich mit der Thematik der immer umfangreicheren, unstrukturierten Datensätzen. Diese stellen eine echte Herausforderung für die Verwaltung älterer Daten dar. Das amerikanische Unternehmen IDC Custom Solutions ist ein weltweit führender...

weiterlesen
Lösegeldzahlung: Fluch oder Segen?
Jede Minute Ausfallzeit bedeutet für Unternehmen viele Tausende Euro an Umsatzeinbußen. Eben diese Problematik ist es auch, die Lösegeldzahlungen nach Ransomware-Angriffen so verlockend erscheinen lässt. Aber: die Ransom-Zahlung ist nicht die schnelle Lösung, auf die Unternehmen bauen. Wer Lösegeld zahlt, erwartet die schnelle Wiederherstellung relevanter Daten....

weiterlesen
Im Januar 2022 befragte ein unabhängiges Forschungsunternehmen mehr als 1.000 IT-Führungskräfte zu den Auswirkungen von Ransomware auf ihre Umgebungen sowie zu ihren IT-Strategien und Datenschutzinitiativen. Die Befragten stammten aus Unternehmen aller Größenordnungen aus über 16 verschiedenen Ländern in APJ, EMEA und Nord- und Südamerika. Dies ist die erste umfassende Marktstudie...

weiterlesen
Angriffe mit Erpressungstrojaners haben in den letzten Jahren stark zugenommen und kosten die deutsche Wirtschaft etliche Milliarden Euro pro Jahr. In einem offenen Brief mit dem Titel “Lösegeldzahlungen bei Ransomware-Angriffen: ein geostrategisches Risiko” fordern IT-Sicherheits- und Informatik-Fachleute nun von den Opfern, den Lösegeldforderungen nicht mehr nachzukommen. Den ganzen Brief finden...

weiterlesen
Die jährlich von Sophos in Auftrag gegebene Studie über Ransomware-Erfahrungen der IT-Experten im Gesundheitswesen deckt eine immer schwieriger werdende Angriffsumgebung auf. Neben der zunehmenden finanziellen und betrieblichen Belastung, die Ransomware für ihre Opfer bedeutet, wirft die Umfrage auch ein neues Licht auf die Beziehung zwischen Ransomware und Cyber-Versicherungen. Dabei geht...

weiterlesen
Auch im Jahr 2022 dominiert Ransomware wieder die Bedrohungslandschaft und entwickelt sich weiterhin zu einem immer komplexeren Geschäftsmodell. Im Vergleich zum Vorjahr hat sich das Volumen der Ransomware-Angriffe fast verdoppelt und die Gesamtkosten von Ransomware wurden auf über 20 Milliarden US-Dollar geschätzt.Was Ransomware so unheimlich und bedrohlich macht, sind mitunter...

weiterlesen
TeleTrusT-Initiative: Zeichen “IT Security made in Germany”
FAST LTA freut sich, zukünftig das markenrechtlich geschützte Vertrauenszeichen “IT Security made in Germany” verwenden zu dürfen. Dieses Zeichen wird interessierten Verbandsmitgliedern auf Antrag und Konformitätserklärung zeitlich befristet bis Ende des laufenden Jahres (Wiederbeantragung möglich) durch TeleTrusT gestattet. Die nachfolgenden fünf Kriterien müssen...
Zur Information: Die TimeStamp Option für Silent Cubes ist ab sofort nicht mehr verfügbar. Mit Übernahme von exceet Secure Solution durch Utimaco ist eine Weiterentwicklung leider nicht mehr möglich.

weiterlesen
Den Großteil ihrer Existenz konzentrierten sich Cybersicherheitsprodukte in erster Linie darauf, bösartigen Code daran zu hindern, auf Computer zu gelangen. Was als Hobbyprojekt zur Beseitigung lästiger Viren auf Disketten begann, hat sich zu einer Multimilliarden-Dollar-Cybersicherheitsindustrie entwickelt, deren Ziel es ist, die mit dem Internet verbundenen Maschinen der modernen Welt zu...

weiterlesen
Die MITRE Corporation registriert die Schwachstellen, die jährlich entdeckt werden, unter einer CVE-ID (Common Vulnerabilities and Exposures). Spezialisten erfassen die Details jeder Schwachstelle und wie sie unter dieser CVE-ID entschärft werden kann. Von diesen entdeckten CVEs werden diejenigen, die industrielle Kontrollsystemumgebungen (ICS) betreffen können, der Öffentlichkeit durch Sicherheitshinweise des Industrial...

weiterlesen
Der diesjährige IBM Security X-Force Threat Intelligence Index zeigt eine unangenehme Wahrheit auf: Unternehmen, Institutionen und Regierungen passen sich weiterhin an einen sich schnell verändernden globalen Markt einschließlich hybrider und Cloud-basierter Arbeitsumgebungen an. Diese durch die Pandemie hervorgerufenen Veränderungen werden von Bedrohungsakteure stetig und mit steigender Tendenz opportunistisch genutzt.Der IBM...

weiterlesen
Der Veeam Data Protection Trends Report 2022 beleuchtet die Datensicherung als den Bereich, in den verstärkt investiert werden wird, um moderne Workloads zu schützen.Die Verbesserung der Datensicherung wird zum großen Teil durch die Erkenntnis vorangetrieben, dass Cyberangriffe, insbesondere Ransomware, für die meisten Unternehmen ein "Wenn" und nicht ein "Falls" sind.
...

weiterlesen
Der Trend führt sich fort: Auch im Jahr 2021 rissen die Nachrichten zu Ransomware-Angriffen nicht ab. Umfangreiche Sicherheitsverletzungen, massive Lösegeldforderungen und Attacken auf Unternehmen jeder Größe und aus den unterschiedlichsten Branchen zogen die Aufmerksamkeit von Medien und Aufsichtsbehörden auf sich, welche im letzten Quartal des Jahres verstärkt auf diese Entwicklungen...

weiterlesen
Wieso heißen unsere Produkte eigentlich Silent Cubes / Bricks?
Man könnte mutmaßen, dass sich "Silent" auf die geringe Geräuschkulisse des Produktes an sich bezieht. Das mag beim Silent Cube noch zutreffen, vor allem, wenn das Speichermodul im Standby ist (da verbraucht es nur 2 Watt). Wer allerdings mal ein Silent...

weiterlesen
Als Geschäftsführer müssen viele wichtige Entscheidungen getroffen und aktuelle Entwicklungen im Blick behalten werden. Der Aspekt der Datensicherung rückt da oftmals in den Hintergrund. Oder er wird als nicht wichtig genug eingestuft, um bei den obersten Prioritäten mitzuspielen. Warum dies ein grober Fehler ist, der schwerwiegende Folgen nach sich ziehen...

weiterlesen
Vorgeschichte:
Bereits 2014 wurde die erste gemeinsame Kundeninstallation zwischen FAST LTA und Veeam realisiert. Hieraus entstand die erste Anbindungsdokumentation zu Veeam V7 mit FAST LTA Silent Bricks, angebunden als Virtuelle Tape Library. Gemeinsame Installationen nahmen seit jeher stetig zu. Ebenso erweiterte sich beidseitig der Funktionsumfang, so dass ab Veeam V9,...
FAST LTA ist sich der kürzlich bekannt gewordenen Sicherheitslücke im Zusammenhang mit dem Open-Source-Apache-Dienstprogramm "Log4j2" (CVE-2021-44228) bewusst. Wir überwachen dieses Problem aktiv.
Betroffene Produkte
Keines unserer Produkte verwendet die betroffene Bibliothek. Unsere Produkte Silent Cubes und Silent Bricks sind von der Log4j2-Sicherheitslücke nicht betroffen.
Aktionen
Da unsere Produkte von der...

weiterlesen
Bei genauer Betrachtung des Themas Datensicherung eröffnen sich drei wichtige Bereiche, die zu Herausforderungen werden können: Komplexität, Langlebigkeit und Sicherheit.
Die große Komplexität in Firmen sowie in der IT-Infrastruktur läuft gegen die Datensicherung. Die Menge an Daten, verschiedenen Datentypen und unterschiedlichen Berechtigungen lassen die Komplexität immer weiter wachsen und stellen...

weiterlesen
Das Bundesamt für Sicherheit in der Informationstechnik (BSI) stellt auch dieses Jahr wieder seinen Bericht zur Lage der IT-Sicherheit in Deutschland vor. Dieser Bericht gibt einen fundierten Überblick über die Bedrohungen im Cyber-Raum und steht auch in diese
m Jahr wieder unter dem Eindruck COVID-19-Pandemie, deren gesamtgesellschaftlichen Auswirkungen auch Folgen...

weiterlesen
Bild: Herr Schramm (hinten rechts), Herr Palmowski (links) und Herr Kleina (sitzend)
Krankenhäuser zählen zu den bedeutsamen Basisdiensten und kritischen Infrastrukturen (KRITIS). Für die IT-Infrastruktur gibt es seitens des Gesetzgebers strenge Vorgaben zur Umsetzung und Datensicherung.Das St. Josef-Hospital Bochum entschied sich schon 2011 für die Silent Cubes von FAST LTA...

weiterlesen
Das zweite Quartal im Jahr 2021 war sehr ereignisreich. Zwar beherrschten hauptsächlich prominente Angriffe die Schlagzeilen, die Mehrheit der Attacken bildeten jedoch jene, von denen der Großteil der Bevölkerung überhaupt nichts mitbekommen hat. In einer kürzlich durchgeführten Umfrage unter 130 Krankenhäusern und Organisationen des Gesundheitswesens, gab fast die Hälfte von...

weiterlesen
Die Kip GmbH, ein weltweit führender Klebebandhersteller für den professionellen Bereich rund um das Maler- und Stuckateur-Handwerk und Baugewerbe mit Sitz in Bocholt, schaffte es nach Gründung 1969 schrittweise zum Global Player mit Produktions- und Vertriebsstandorten auf der ganzen Welt. Das Unternehmen, welches seit über 50 Jahren erfolgreich am Markt...

weiterlesen
Mitte August kam es in den USA erneut zu einem Hacker-Angriff auf ein amerikanisches Unternehmen: Poly Network, eine Firma, die auf den Transfer von Kryptowährungen spezialisiert ist, gerieten ins Netz der Hacker. Diese stellten dabei eine Summe in Höhe von 600,3 Millionen Dollar sicher - der größte Krypto-Diebstahl der Geschichte....

weiterlesen
Es steht außer Frage, dass 2020 ein herausfordendes Jahr war - für Unternehmen wie auch für Privatpersonen. Die Pandemie stellte eine enorme Belastung für die Weltwirtschaft dar, was Cyberkriminelle zu ihren Zwecken nutzten und zu vermehrten Angriffen führte. Der 2021 Voice of CISO Report von Proofpoint befragt 1.400 CISOs (Chief...

weiterlesen
“2021 wird das Jahr der Erpressung.” Diese düstere Prognose äußerten Cyber-Experten im Acronis Cyberthreats Report 2020 von Dezember letzten Jahres. Dass diese Vermutung nicht unbegründet ist, zeigen zahlreiche Fälle allein in den letzten 7 Monaten. Die Cyber-Kriminalität steigt stetig und Ransomware-Attacken belasten inzwischen auch zunehmend deutsche Unternehmen und Organisationen, welche...

weiterlesen
Phishing gilt in vielerlei Hinsicht als älteste Cyberbedrohung der Welt. Die ersten Angriffe wurden von Kriminellen durchgeführt, die sich als AOL-Mitarbeiter ausgaben und Bestätigungen von Rechnungsadressen bei Unternehmen einforderten.
Der Begriff tauchte dazu 1996 in einer Usenet-Newsgroup namens AOHell erstmals auf. Das Kunstwort beschreibt bildlich das Angeln nach Passwörtern, wobei...

weiterlesen
Zwei neue Ransomware-as-Service (RaaS)-Programme sind im Juli auf dem Cybercrime-Radar aufgetaucht. Die Gruppe BlackMatter behauptet, ein Nachfolger von DarkSide und REvil zu sein. Die beiden berüchtigten Ransomware-Syndikate waren nach den Großangriffen auf Colonial Pipeline und Kaseya in den letzten Monaten vom Netz gegangen. Bei der zweiten Gruppe Haron spekuliert man...

weiterlesen
Ein Hackerangriff legte Anfang Juli die Verwaltung des Kreises Anhalt-Bitterfeld lahm. Der Pressesprecher der Landkreisverwaltung bestätigt, dass aufgrund eines Cyberangriffs auf das gesamte IT-System aller Standorte der Kreisverwaltung am 09. Juli 2021 alle kritischen Systeme vom Netz genommen wurden.Erster Cyber-Katastrophenfall ausgerufen
Der deutschlandweit erste Cyber-Katastrophenfall für den Landkreis Anhalt-Bitterfeld wurde...

weiterlesen
Durch einen Hackerangriff wurden Anfang Juli weltweit tausende Firmen lahmgelegt, darunter auch deutsche Unternehmen, welche mit gerade mal 3,2% Infektionsversuchen jedoch nur einen geringen Anteil ausmachten. Jede vierte Attacke hingegen zielte auf die USA. Auch die schwedische Supermarktkette Coop wurde stark von dem Angriff getroffen. Hier fielen alle Kassensysteme aus,...

weiterlesen
Die Websites im Darknet der mit Russland in Verbindung gebrachten Ransomware-Gang REvil, die für Angriffe auf Hunderte von Unternehmen weltweit verantwortlich gemacht wird, sind offline gegangen.Beobachter berichten, dass eine Zahlungswebsite und ein Blog, die von der REvil-Gruppe betrieben werden, am Dienstag plötzlich nicht mehr erreichbar waren. Der Grund für das...

weiterlesen
Der Bundesrat hat nach monatelangen Verhandlungen und mehrmaligen Abstimmungsverschiebungen eine Neufassung des Bundespolizeigesetzes zwar bislang mehrheitlich abgelehnt und das Projekt vorerst - zumindest teilweise - gestoppt, jedoch kann mittels eines Vermittlungsausschusses noch Einigung und damit die Durchsetzung des Gesetzes erzielt werden.
Dieses Gesetz sieht den Einsatz von Staatstrojanern auch...

weiterlesen
Kryptowährung ist nicht nachverfolgbar, und Zahlungen sind demnach anonym?Ein verbreiteter Irrglaube, denn Bitcoin-Transaktionen lassen sich sehr wohl tracken - wenn auch mit einigem Aufwand verbunden. Die Blockchain-Technologie ist eine öffentliche zugängliche Datenbank, mit der zu jeder Zeit von jedem Menschen alle jemals getätigten Transaktionen nachverfolgt werden können. Obwohl die jeweiligen...

weiterlesen
In einer live gestreamten gemeinsamen Pressekonferenz teilten das US-Justizministeriums (Department of Justice - DoJ) und das FBI mit, dass Kryptowährung im Wert von 2,3 Millionen US-Dollar sichergestellt wurde. Dabei handele es sich um den Großteil des Lösegeldes aus der Colonial Pipeline-Cyberattacke, das an die Ransomware Erpresser DarkSide bezahlt wurde.
Hintergrund...

weiterlesen
Viele Filme und andere Medien haben eine womöglich etwas verzerrte Vorstellung davon, was Hacker genau machen. Aber eine Serie zeigt es richtig: Mr. Robot. Hier wird klargestellt, dass die schwächste Stelle eines Unternehmens in der Regel seine Mitarbeiter sind. Der sogenannte „menschliche Faktor“.Viele Datenschutzverletzungen und andere Sicherheitsprobleme hätten vermutlich vermieden...
weiterlesen
Was ist Ransomware?
Der Begriff Ransomware steht für eine Spezies von Schadprogrammen, die den Zugriff auf Daten und Systeme einschränken oder ganz unterbinden. Für die Freigabe wird daraufhin ein Lösegeld (englisch: ransom) verlangt. Auch die Bezeichnung "Erpressungstrojaner" ist daher geläufig. Entweder sperrt ein solches Schadprogramm den kompletten Zugriff auf das...





